How I Found CVE-2021-29115 with FFUF in a few minutes
Greetings everyone. Today, I want to tell you how I found CVE-2021-29115, which is an Information Disclosure vulnerability, in a bug bounty program in just a few minutes. To keep things anonymous, let’s call the target website “redacted.com.”
To begin my exploration, I used a subdomain enumeration tool named Subfinder. This tool helped me find any subdomains linked to redacted.com.
1
$ subfinder -d redacted.com
Once I had put together a list of subdomains, I picked one and started exploring content using the ffuf tool. I ran this command:
1
$ ffuf -u https://subdomain.redacted.com/FUZZ -w dicc.txt
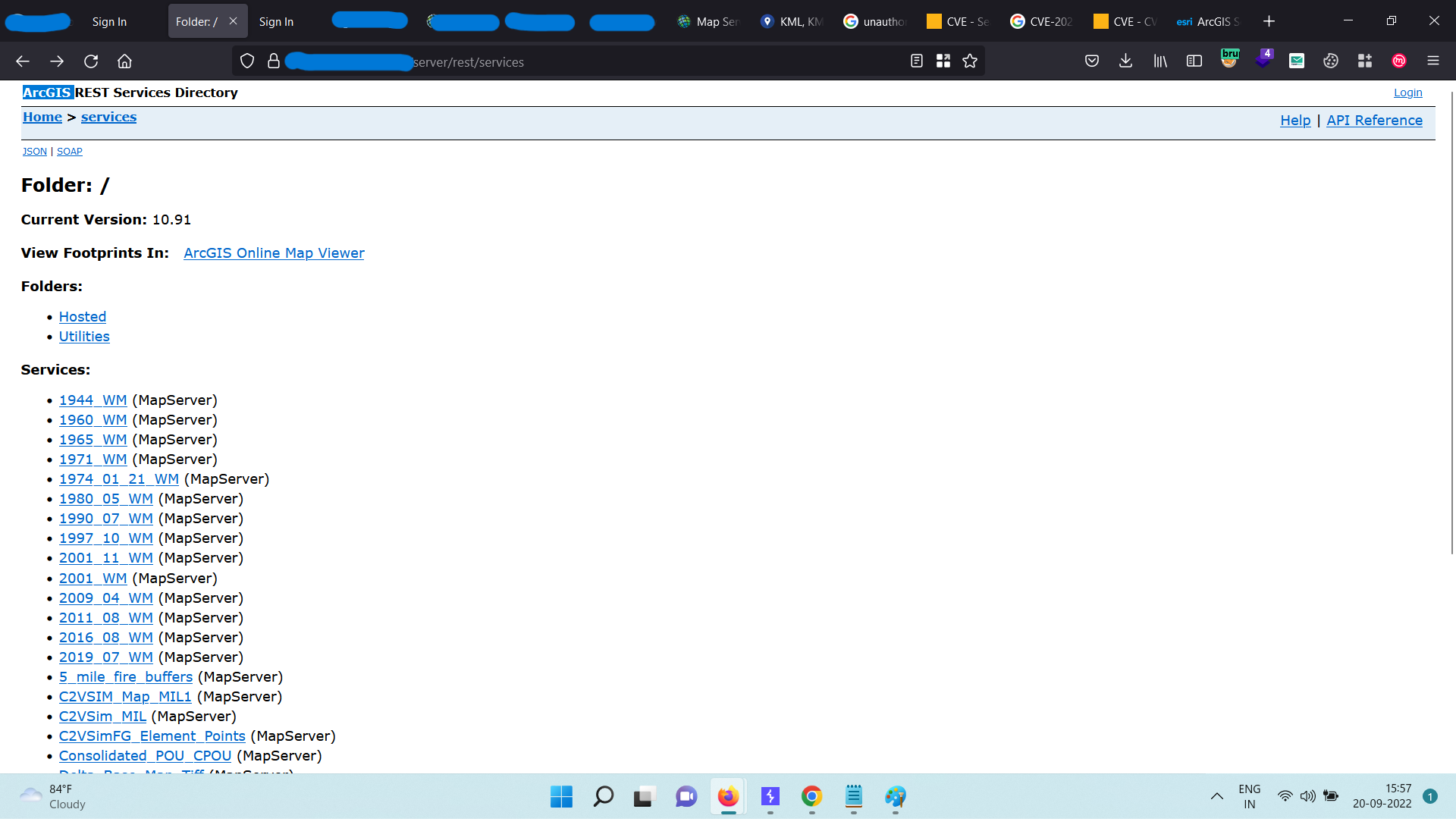
As I ran the scan, I discovered something interesting: the endpoint /server returned a 301 redirect status. Intrigued by this redirect, I tried to access the endpoint in my browser. It quickly redirected me to the following endpoint: /server/rest/services.
This caught my interest, so I began to look into the /server/rest/services endpoint more closely. Through some testing, I found that the endpoint had an Information Disclosure vulnerability (CVE-2021-29115). This flaw allowed me to access sensitive information about the application and its environment.
I reported this vulnerability to the bug bounty program and earned a Hall of Fame recognition for my findings. This shows how a few simple tools and some persistence can lead to a successful bug bounty hunt!
Vulnerability Report:
Description
An information disclosure vulnerability in the ArcGIS Service Directory in Esri ArcGIS Enterprise and below may allows a remote attacker to view hidden field names in feature layers. This issue may reveal field names, but not disclose features.
Steps To Reproduce:
Navigate to https://Redacted.com/server/rest/services
Supporting Material/References:
Navigate to https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-29115